Security Basics
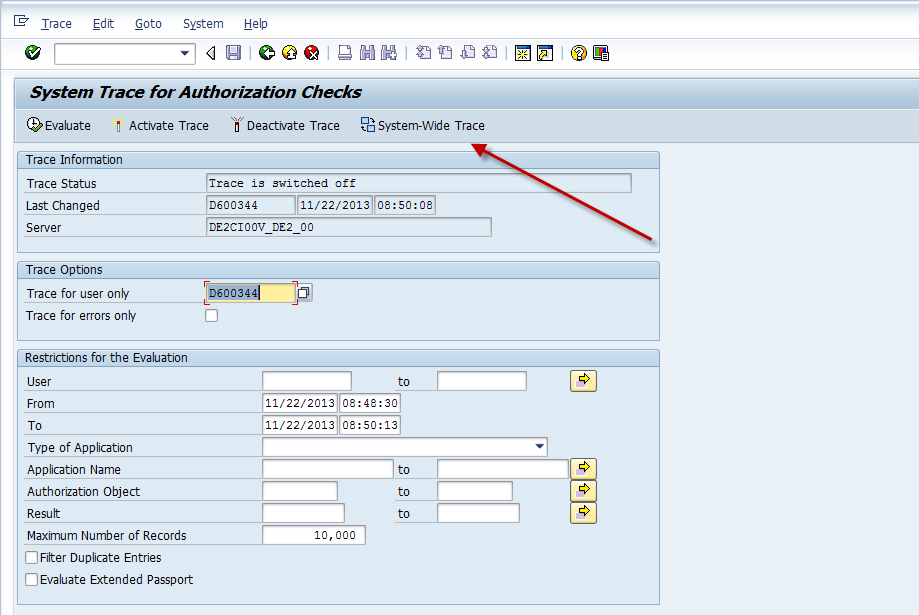
STAUTHTRACE
Maybe I am being cynical here, but I would still say that its very rare that SAP comes up with
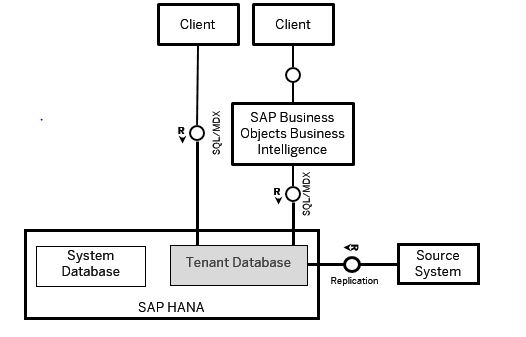
BW and BOBJ
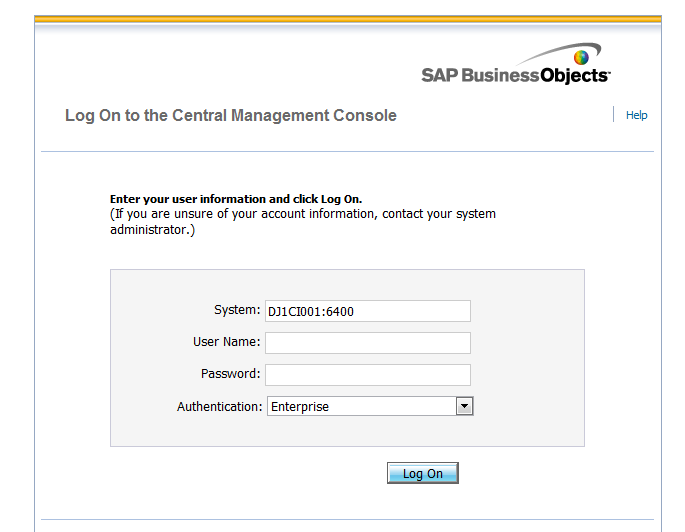
SAP Authentication in CMC
Till now we have created users and group in the CMC and mapped these groups to application and content rights.
HCM
HR Processes and Forms
A growing tendency of HR departments around the world has been to decentralize the maintenance of HR data. So instead