Authorization Trace in BW
The standard SAP authorization trace given by ST01 is not enough for troubleshooting security issues in BW reporting. A ST01 trace will show a basic reference for the two objects S_RS_COMP and S_RS_COMP1 to check access to the query and cube but nothing further than that. SAP provides a completely new authorization trace though the RSECADMIN transaction to troubleshoot analysis authorizations. The error log button gets us to the authorization trace screen.
Once we have “configured log recording” for the affected user, the system logs all OLAP data accesses made by the user.
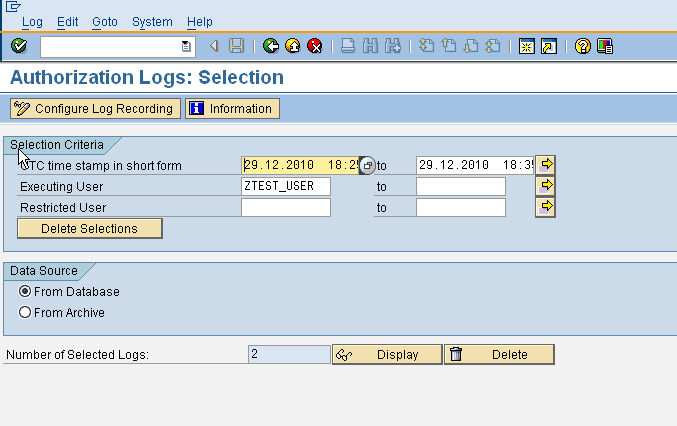
Displaying the log data gets us into the following screen which shows the details of the security checks for the user.
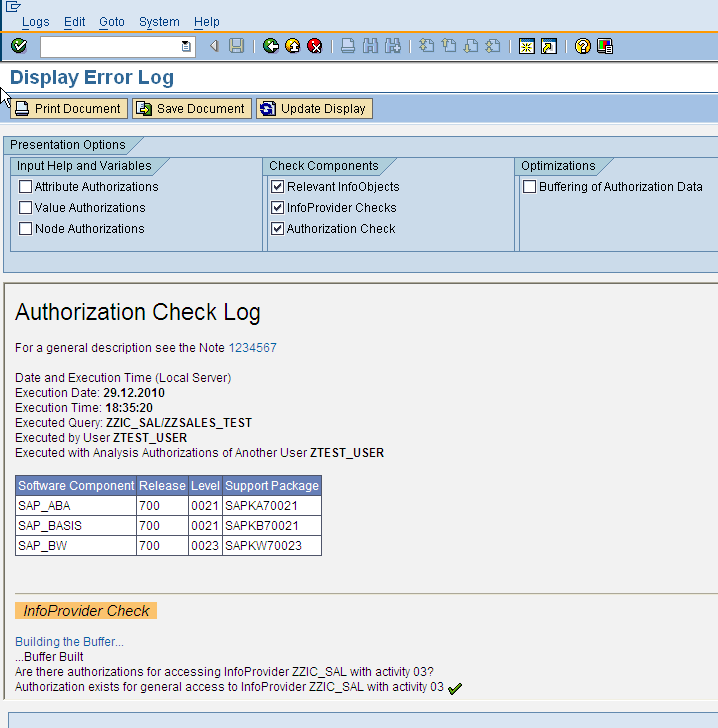
The trace first displays the name of the InfoProvider and the query name that the user executed. Next, we have a list of characteristics in the cube for which user has non full (*) access as these need to be checked at a more detail level. Lastly we have the authorization checks for these characteristics with non full authorizations. Its this section of the trace thats typically the most helpful in troubleshooting authorization issues.
Hi Aninda,
Firstly, thanks for the helpful posts on this site.
I would like to check with you on how the system checks BI auth.
Does it check every possible combination?
For eg: user is assigned with 2 analysis auth as below:
A: plant 1000, purchasing group (PG) 100
B: plant 2000, PG 200
When the user runs a report and fills in the fields with plant : 1000, 2000 and PG: 100, 200,
he/she will actually get no authorization. When I checked the trace, it looks like the system is checking for
1) plant 1000, PG 100
2) plant 1000, PG 200
3) plant 2000, PG 100
4) plant 2000, PG 200
In this case, the authorization failed because there is no such combination for 2 and 3 in my analysis authorization. Appreciate your advice if my understanding is correct and how do we work around this apart from asking the user to run the report separately for plant 1000 and 2000? Thanks.
Hi Jo,
First of all, let me thank you for asking such a great question. Understanding the behavior of the SAP security system in different scenarios is likely to benefit others visiting the post.
Now to your question. Your interpretation about how the system is actually behaving is absolutely correct. System checks that you have access to all 4 combinations before giving you access. So with the two authorizations that you have, you will face an authorization error. The easy workaround for this as you mention is to ask the user to run the report twice with the different combinations of values. To help the user, you can actually save the combinations in two variants and ask that these be used instead of manually keying in the values.
Finally, I am not sure if you just picked up an example with the above scenario or are actually trying to solve a business requirement. If this is an actual requirement, you might want to check the enterprise structure (the relationships between plants, purchasing groups and users) in your organization. Typically I have found that buyers are assigned to purchasing groups and might be responsible for one or more plants. So the requirement that a buyer should have different purchasing groups for different plants is a bit different from what I have seen till now. If after further research you find that that the buyer is really responsible for PG 100 and 200 in Plants 1000 and 2000, the best solution would be to create a single authorization with Plant 1000, 2000 and PG 100, 200 instead of the two that you are currently using.
Regards,
Aninda
Exactly what I wanted to see, thanks for writing it.
Hi Aninda,
Will logs be generated everytime? I mean to say like ST01 does trace in BI also shows log if authorization is sucessfull?
Thanks,
Nitin
You will get the log but not details on which characteristics are getting checked.
Hi Aninda
1. Does St01 reports missing values of s_rs_auth object .
2. What is that restricted user ?
Hi Syed,
For missing S_RS_AUTH objects i.e. Analysis Authorizations, you would need to use the trace function in the RSECADMIN transaction. I am not sure about your second question though.
Thanks,
Aninda
Hey while executing t.code RSUDO – Execute as user with restricted authorizations when I try to execute on behalf of other user, system is asking for password.
Can you tell the reason for it?
Thanks
Hi Saur,
Password is asked in process of authentication as you are logging as the different user.
Thanks
Hi Aninda,
Can you please explain the use of Type and the Validity area in tracing, and how these are related to nodes.
Thanks in advance.
Trilok
Thanks for your informative writing.
Hi..
Is there is a way to find the relation b/w infocube and infoarea other than RSA1.
Thanks